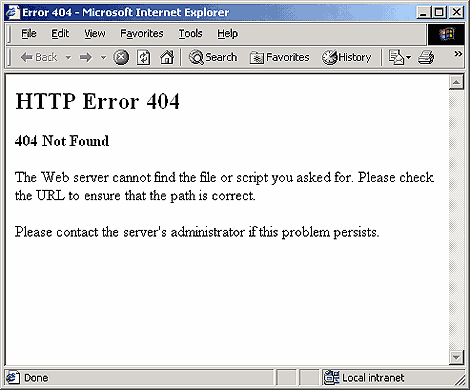
- Retry the web page by pressing F5, clicking the refresh/reload button, or trying the URL from the address bar again.
The 404 Not Found error might appear for several reasons even though no real issue exists, so sometimes a simple refresh will often load the page you were looking for.
- Check for errors in the URL.
Often times the 404 Not Found error appears because the URL was typed
wrong or the link that was clicked on points to the wrong URL.
- Move up one directory level at a time in the URL until you find something.
For example, if www.web.com/a/b/c.htm gave you the 404 Not Found error, move up to www.web.com/a/b/. If you get nothing here (or an error), move up to www.web.com/a/. This should lead you toward what you're looking for or at least confirm that it's no longer available.
Tip: If you have moved all the way up to the website's homepage, try to run a search for the information you're looking for. If the site doesn't have a search function, try navigating to the page you want using category links to dig deeper into the site.
- Search for the page at a popular search engine. It's possible that you simply have the entirely wrong URL in which case a quick Google or Bing search should get you where you want to go.
If you do find the page you were after, update your bookmark or favorite to avoid the HTTP 404 error in the future.
- Clear your browser's cache
if you have any indication that the 404 Not Found message might just be
yours. For example, if you can reach the URL from your phone but not
from your tablet, clearing the cache on your tablet's browser might
help.
You might also consider clearing your browser's cookies, or at least the one(s) involved with the website in question, if clearing the cache didn't work.
- Change the DNS servers
used by your computer but usually only if an entire website is giving
you a 404 error, especially if the website is available to those on
other networks (e.g. your mobile phone network or a friend in another
city).
404's on an entire website isn't particularly common unless your ISP or government filters/censors websites. No matter the reason, if it does happen, giving another set of DNS servers a try is a good step to take. See my Public DNS Servers List for some alternatives.
- Finally, if all else fails, contact the website directly. If they've removed the page you're after then the 404 error is completely legitimate and they should be able to tell you that. If they've moved the page, and are generating 404's instead of redirecting visitors to the new page, they might be very happy to hear from you.
Attention:
- Don't delete entire logfiles, instead, just remove only the incriminating entries from the file. The other question is, is there a backup logfile? What if they just look for differences and find the exact things you erased? Always think about your actions. The best thing is to delete random lines of log, including yours.
- Be extremely careful if you think you have found a very easy crack or a crude mistake in security management. A security professional protecting that system may be trying to trick you or setting up a honeypot.
- Although you may have heard the opposite, don't help anyone patch their programs or systems. This is considered extremely lame and leads to being banned from most hacking communities. And if you would release a private exploit someone found, he may become your enemy — and he's probably better than you are .
- Never do anything just for fun. Remember it's not a game to hack into a network, but a power to change the world. Don't waste that on childish actions.
- Misusing this information may be a local and/or federal criminal act (crime). This article is intended to be informational and should only be used for ethical - and not illegal - purposes.
- Hacking into someone else's system may be illegal, so don't do it unless you are sure you have permission from the owner of the system you are trying to hack or you are sure it's worth it and you won't get caught.
- If you aren't confident with your skills, avoid from breaking into corporate, government, or military networks. Even if they have weak security, they could have a lot of money to trace and bust you. If you do find a hole in such network, it's best to hand it to more experienced hacker that you trust who can put these systems to good use.
What you will need?
- A (fast operating) PC or laptop with a connection to the Internet.
- A Proxy (optional)
- An IP scanner
- Petaflops Help
Test the target.
Can you reach the remote system? While you can use the ping utility (which is included in most operating systems) to see if the target is active, you can not always trust the results — it relies on the ICMP protocol, which can be easily shut off by paranoid system administrators.
Determine the operating system (OS).
Run a scan of the ports, and try pOf, or nmap to run a port scan. This will show you the ports that are open on the machine, the OS, and can even tell you what type of firewall or router they are using so you can plan a course of action. You can activate OS detection in nmap by using the -O switch.
Find a path or open port in the system.
Common ports such as FTP (21) and HTTP (80) are often well protected, and possibly only vulnerable to exploits yet to be discovered.
- Try other TCP and UDP ports that may have been forgotten, such as Telnet and various UDP ports left open for LAN gaming.
- An open port 22 is usually evidence of an SSH (secure shell) service running on the target, which can sometimes be brute forced.
Know your target.
The process of gathering information about your target is known as enumeration. The more you know in advance, the fewer surprises you'll have.
Use a *nix terminal for commands.
Cygwin will help emulate a *nix for Windows users. Nmap in particular uses WinPCap to run on Windows and does not require Cygwin. However, Nmap works poorly on Windows systems due to a lack of raw sockets. You should also consider using Linux or BSD, which are both more flexible, more reliable, and more secure. Most Linux distributions come with many useful tools pre-installed.
Secure your machine first.
Make sure you've fully understood all common techniques to protect yourself. Start with the basics — have you found a server hosting a site about illegal or possibly bad activity? Attempt to hack it in any way you can. Don't change the site, just make it yours.
The process of gathering information about your target is known as enumeration. The more you know in advance, the fewer surprises you'll have.
Use a *nix terminal for commands.
Cygwin will help emulate a *nix for Windows users. Nmap in particular uses WinPCap to run on Windows and does not require Cygwin. However, Nmap works poorly on Windows systems due to a lack of raw sockets. You should also consider using Linux or BSD, which are both more flexible, more reliable, and more secure. Most Linux distributions come with many useful tools pre-installed.
Secure your machine first.
Make sure you've fully understood all common techniques to protect yourself. Start with the basics — have you found a server hosting a site about illegal or possibly bad activity? Attempt to hack it in any way you can. Don't change the site, just make it yours.
Facebook developer team included new additional feature in their
database algorithm which is called embed post. This splendid feature has
been updated in Facebook recently a month ago. how Facebook embed post
work and how to use this ?. Facebook Embed post allow us to take or
select your desire post from Facebook and insert anywhere in the blog or
website. On adding Facebook status post in your blog it will show
dynamically and will react same as it was shared on Facebook. Sometime
you might be wondering to show the Facebook entertainment activities on
your blog or website dynamically for your readers and lovers. So one of
our reader asked how to add or display Facebook share posts dynamically
along with status in blogger blog. In today article we will show you how
to embed Facebook posts status in blogger.
Embedded Facebook Post Status In Blogger
Facebook bring awesome opportunity to bloggers and webmasters to share
their love, discussion and posts on blog or website. Now you can
comfortably share your facebook publish post on your blog or website in
less than a minute. To do so you must be remembered that your post
should must be public on facebook. Select your public posts in facebook
to share on your blog because rather than public mode there having
facebook strictly forbidden to do share.
First You need to login in your facebook account >> Go to your facebook page and select your desire post which you want to share on your blog. The post should must be publicly shared on facebook.
After Selecting your desire post just click on the right side 'tick
mark' option which show on the right side to the front of the post
title. On clicking you will see drop down menu and then click on embed
post.
when you click on embed post a new small window will appear along with codding as you see in the below screenshot.
Copy the entire code >> Now inside blogger post editor click on HTML and past the post coding where you want to display the facebook post. So after publishing or previewing your post you will see the embedded post on your post. I did not add this here because it will compel my page on loading time.
Our today recipe will all about google adsense earning. As we all know
Google Adsense is a famous CPC program through which thousands and
millions of Bloggers are earning money every month. However, few are
complaining that their revenue is not enough yet. So this guide is for
those who haven’t had any luck with the program but they still have a
desire to go on with it. I will teach you how to skyrocket your Google Adsense earning
by following few useful steps. Results won’t increase by some 100% but
I guarantee that you will see some improvements gradually in the
earning. So in today article we will show you how to increase google adsense earnings revenue by applying the below top killer strategies.
5 killer Way To Increase Google Adsense Earning
Apply all these pro 6 killer strategies on your Blog to boost your adsense earning.
Popularize Your Posts Building Baklinks & Increase Revenue
Backlinks play important role in improving your website’s performance in the search engine.
Now question is what to do and how to improve your position in the search results. The only answer is making more and more backlinks. Find Do Follow Blogs in your niche and post sensible comments.
You can also join do-follow forums and contribute in the discussion for earning some valuable link back to the website. Use your keyword as an anchor text in the signature and try to post as much as you can.
Conclusion: After follow the above strategies at the movement you have loyal readership, massive traffics and dozens of pagesviews, now i would say there is no doubt to grab handsome money by Google Adsense.
Now question is what to do and how to improve your position in the search results. The only answer is making more and more backlinks. Find Do Follow Blogs in your niche and post sensible comments.
You can also join do-follow forums and contribute in the discussion for earning some valuable link back to the website. Use your keyword as an anchor text in the signature and try to post as much as you can.
Conclusion: After follow the above strategies at the movement you have loyal readership, massive traffics and dozens of pagesviews, now i would say there is no doubt to grab handsome money by Google Adsense.
Write Awesome Articles
It’s not an old saying that content is the king! I will rather say it
acts like a soul for your blog. What happens to the body without soul?
You know it better, right? So, your blog is almost like a dead body
without creative and engaging content.
Do proper research on the topic you are planning to attempt and provide
your personal insights along with accurate details and information to
the readers. Include images and infographics to beatify your
posts and making them more attractive. Don’t just construct a wall of
content in the post; readers don’t like reading long, boring articles.
Formatting your article is also crucial in blogging; use headings,
subheadings, quotes and conclusions.
Conclusion: So the more you have unique quality contents the more you have chances to built strong readerships + Traffics + Maximize Adsense Earnings.
Conclusion: So the more you have unique quality contents the more you have chances to built strong readerships + Traffics + Maximize Adsense Earnings.
Ad Placement and Position:
The placement of Adsense ad-blocks matter a lot in boosting the blog
earning. I know couple of impatient bloggers who have filled every inch
of their post with ads everywhere.
Do you think it’s a good idea to make your post crowded and cluttered?
No, it’s not. Try to use no more than three ad units on the blog and
place each block in a good position, especially on the pages where you
are getting high traffic.
The right ad placement will prevent accident and fraudulent clicks, as a
result your CTR may jump up from 0.56 % to 5 % and even higher. If you
don’t want to put your blog on Google radar you have to be rational when
displaying ads on the blog. And this implies to all other third party
advertisements that you are showing right now.
Display all Types of Ads:
Never try to limit ad visibility to text ads only as this may lower your
CPC. Use all types of ads in suitable locations in your blog to get
maximum exposure and higher bids from advertisers; text, Media Rich ads,
Banner, and image ads, all should be considered when it comes to
displaying Adsense codes in the blog.
Always try to keep your affiliated & adsense banners as low as possible. Do not turn your blog into fish market it would not help in increasing your adsense revenue, instead it would discourage your blog readership and also compel your blog on loading time.
Always try to keep your affiliated & adsense banners as low as possible. Do not turn your blog into fish market it would not help in increasing your adsense revenue, instead it would discourage your blog readership and also compel your blog on loading time.
Search High CPC keywords:
Do a little homework on searching the keywords with high CPC, high
traffic volume and low competition. You can use Adword Keyword tool to
filter your search on a specific niche or subject. Of course, keywords
with high CPC will generate more earning in the account, but overuse any
search term or Google will consider you a spammer. Blend your keyword
wisely within content and let your post be natural in the tone.
Howto : Source -- Problogger
Choosing right domain is the key to success for every blogger. Every new blogger when come to decide to pick a good domain name for website then its becomes very difficult and challenging when there are so many best domain names already exists and they and taken by web gurus. So if you are new to internet world and hunger for choosing the domain then follow our tips and will probably help you, i am not sure that it will complete all your criteria but it will absalutly analize your thought and will be able to find its quickly. Remember these points mentioned below & try your self...
Domain Must Describe Your Blog
When visitors landing on your blog they will read your blog title, address, if your domain describe the whole blog then visitor will easily understad whats the blog about and will become easy to remember. So pick domain thats relate to your blog.There Should Be Keywords in Domain Name
There should be keywords in your domain name try to add more important keywords in your blog it is a good practice because when people search your blog from search enginge but if they want to re visit your blog if your blog title and name match with domain name then it would be better and resgister such type of domain but its so hardy work try try again to get your exact domain. but if your domain name does not meet with your blog keywords then you may loss some visitors specially from search engine.Search for Popular Domain Name
It is very very intersting because in this way you can easily collect the attention of millions of people and they will visits your blog without by any external links or vidoes tutorials but specially from search engine. Choosing a popular blog similar domain name in your niche. For example if you niche is blogging or then there is blog we say problogger.net now you to recustomize it by adding or subtracting keywords so now you have problogggertricks or problogging.com etc...in this way visitors can see your blog below the popular blog and will must visit your blog.Try To Short and Avoid Hyphens
Always try to be short your domain because it can easily remembered.. But i would strongly recommended to you never use hyphens - or numerical value in your domain it can be effected for example if you use hyphens like this pro-bloggertricks.com and then it should be difficult to remember with hyphens always be try to get good domain name without hyphens numericals value like my123blogger.com it is ideal..no way to rank your blog in searh engine.Choose a .com Domain Name
.com has high priority then all others first try to deal with .com but if does,nt available then goes for .net or org.Google Analytical Tools Helper
So it is very difficult to get a good domain name while searching and wasting your time in searching but there is a great and amazing online tools that will help you and by which you can get easily domain name with your keywords. Go to google analytical tools type your keywords it will show all the words related to your blog now choose that one which has high rank in search engine..it must helped you and will give you thousnads of keywords if you have no idea about keywords thats meet your blog.Online Tools For Checking Domain
Hare is the list of website through which you can easily type and see the result weather this domain exist or not. Domainr , GoDaddy, Centralops ,WhoisSoftware : source -- http://www.kali.org/downloads/
Earlier I wrote about BackTrack renaming itself as Kali Linux or BackTrack 6 will be available for download soon, today is the day when all hackers and Backtrack users can download Kali Linux.
Backtrack development team had announced that they are in process of a major change and the operating system, that will be replaced by the name of Kali.
Kali Linux is based upon Debian Linux, instead of Ubuntu and new streamlined repositories synchronize with the Debian repositories 4 times a day, constantly providing users with the latest package updates and security fixes available.
You can download Kali from Free ISO (image) and password is toor.
News : Source by http://hackread.com
Chicago based Jeremy Hammond linked to the online hacktivist group Anonymous and has been sentenced on Friday to ten years in prison for cyber attacks against various government agencies of the U.S. government and financial giants, including Strategic Forecasting, Inc., more commonly known as Stratfor.
Jeremy Hammond, 28, was convicted of cyber attacks on he conducted on Stratfor in December 2011, which his lawyers claim to have been motivated by concerns about the role of private companies in collecting intelligence information at home and abroad.
Prosecutors said the attack on Strategic Forecasting, or Stratfor, resulted in the theft of 60,000 credit card numbers and data from 860,000 customers, which were later posted on the Internet.
In March 2012, FBI had changed AntiSec’s Jeremy Hammond with information equals $700,000 in Startfor hacking.
It all started with a ex-anonymous and a snitch SABU who sold out the personal details of Jeremy Hammond to FBI in 2012.
News : Source -- http://www.techienews.co.uk/
A group of hackers linked with the notorious Anonymous hacking collective have pleaded guilty in the 2010 PayPal Distributed Denial of Service (DDoS) attack.
Out of the thirteen hackers, ten pleaded guilty to one count of conspiracy and one count of damaging a protected computer, while the remaining pleaded guilty to one count each related to the attack. The ten will be allowed to change their felony charges to misdemeanor next year if they comply with the terms of their agreement till their sentencing.
According to the statement released by U.S. Attorney Melinda Haag, District Judge D. Lowell Jensen will announce the sentences starting November.
The group was responsible attacking PayPal’s servers through a DDoS attack after eBay’s unit suspended account of WikiLeaks.
EBay chairman Pierre Omidyar has asked the government to show leniency while issuing sentences to all those who have plead guilty in the case. The Department of Justice might be looking for a serious jail time; however, Omidyar has appealed to the feds to go easy on the bunch.
Through an editorial on the Huffington Post, Omidyar said that he understood the reasons behind the protests and he “felt that they were simply participating in an online demonstration of their frustration.”
“That is their right, and I support freedom of expression, even when it’s my own company that is the target,” he said.
Omidyar acknowledged that DDoS are serious enough attacks, but there is a disparity in prosecuting and crime for this particular act. Omidyar said that instead of jail time backed by felony charges, the defendants should be asked to pay fines under misdemeanor charges.
Are you play candy crush? here you can use Free Candy Crush Saga Hack
Cheats If you
think you really have to be ahead of your competition because like me I am very
impatient and I don’t want to be defeated you can call me a cheater and don’t
play according to the rules. I know what you are thinking that you don’t
deserve to play the game but I don’t care as long as I am able to win the
game using Candy
Crush Saga Hack Cheats its
OK with me. But my question is why are you visiting this page?
Am
sure, you are also looking forCandy Crush Saga Hack Cheats. Well am not going
to disappoint you but let me get this straight that if you search online like
search engine or YouTube you can find so many niche like this that talks about
how their cheat engine works but not all of them works well. But here we have
spend time coding and testing it until we can full provide the real working
Candy Crush Saga hack cheats Engine its really takes time to get this done but
We don’t care as long we can produce what people are looking for to get ahead
of their competition or their classmate when playing this Candy Crush Saga
Facebook game
Instructions:
1. Get as Many LIVES you want
2. Unlimited Lollipops
3. Use it anytime you want
4. 100% Save and Virus free
5. Can be use for iOS, Android, Windows, Linux and Mac
6. Automatic Update
Movie : Source -- http://www.youtube.com/
Track Down (also known as Takedown outside
the USA), is a 2000 film about computer hacker Kevin Mitnick, based on the book Takedown by John Markoff and Tsutomu Shimomura. The film was directed by Joe Chappelle and
stars Skeet Ulrich and Russell Wong
Let's Watch


























.jpg)

